Data centres and cybersecurity - what to look at from an EU, UK and a Saudi Arabian perspective?
With the increasing focus on data security and network resilience, data centre operators need to be aware of and ready to comply with new strengthened cybersecurity obligations. We are witnessing a trend of increasing regulation in this area, with EU Member States now working on the transposition of the NIS2 Directive into their local laws (see our NIS2 Directive Implementation Tracker). The updated EU cybersecurity regime will apply from 18 October 2024 and has a direct impact on data centres. We a brief overview of the key elements and how to prepare for it. We also cover developments in the UK and the Kingdom of Saudi Arabia.

EU – new strengthened cybersecurity regime under the NIS2 Directive and national implementation applies to data centres – what do you need to do?
The key elements of the NIS2 regime (which strengthens and replaces the existing regime) are as follows:
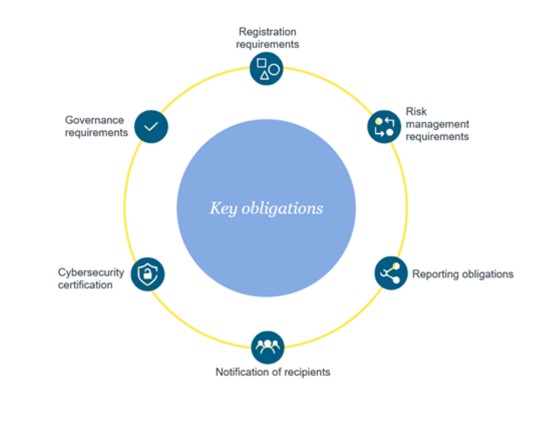
- Registration requirements: Data centre operators will need to submit certain information to the competent authorities in connection with their registration obligations.
- Strengthened cybersecurity risk-management requirements: companies will need to have certain measures in place (e.g., measures regarding incident handling, business continuity, supply chain security, human resources security, access control policies and asset management) to manage the risks to the security of the network and information systems.
- More detailed reporting obligations: Incident reporting obligations to competent authorities and operators may also need to notify customers in certain cases.
- Cybersecurity certification: For the purposes of demonstrating compliance with cybersecurity risk-management measures, Member States may require data centre operators to use particular ICT products, services and processes, either developed by the essential or important entity or procured from third parties, that are certified under European cybersecurity certification schemes.
- Explicit governance requirements: Senior management boards and committees will be required to approve and oversee the implementation of the cybersecurity risk-management measures. In addition, the members of company management bodies will be required to follow training and shall encourage entities to offer similar training to their employees on a regular basis.
- Accountability of top management, supervision and enforcement: The regime also introduces accountability and liability of top management for the non-compliance with cybersecurity obligations, more stringent supervisory measures for national authorities as well as stricter enforcement requirements and aims to harmonise sanctions regimes across Member States.
- Administrative fines: fines of a maximum of at least 10 000 000 EUR or of a maximum of at least 2% (of the total worldwide annual turnover in the preceding financial year can be imposed for non-compliance, whichever is higher).
What should data centre operators do now
- Carry out a scoping exercise to determine the applicability of the regime to your organisation;
- Track and analyse the local NIS2 implementation in the countries of interest;
- Review current processes and procedures to assess what changes need to be made to align with the new requirements;
- Update incident response plans and processes, including those aimed at compliance with other laws, such as the GDPR, data breach reporting and telecoms reporting requirements;
- Draft a practical compliance plan with specific target dates;
- Review and update your contract with your service providers and suppliers;
- If you deal with customers operating in a financial sector, there may be additional requirements to consider, for example the application of the Digital Operational Resilience Act which addresses cybersecurity risks in the financial sector and impact ICT third party suppliers;
- Ensure that regulatory efforts in related areas (IT contracts, privacy, sector specific laws) are consistent.
UK - What are the key obligations under the UK cybersecurity regime?
Given Brexit, the UK is not required to implement the new NIS2 Directive and instead the old NIS regime as currently implemented in the UK under the Network and Information Systems Regulations 2018 remains in place.
This applies to:
- Operators of essential services
- this relates to providers of services that are essential for the maintenance of critical societal or economic activities (e.g. water, energy, transport, health and digital infrastructure); and
- this relates to providers of services that are essential for the maintenance of critical societal or economic activities (e.g. water, energy, transport, health and digital infrastructure); and
- Relevant digital service providers – this covers providers of online search engines, online marketplaces, and cloud computing services – it does not directly apply to data centre operator unless they provide cloud computing services which may include cloud hosting services (if offered by data centre operators).
Notwithstanding this, the UK is proposing to expand the scope of this cybersecurity regime to cover managed service providers (noting that telecoms services will remain subject to the separate telecoms security regime in the UK). However, the changes have not been adopted yet and we are awaiting implementing legislation.
To the extent that data centre operators are providing services that are captured by the NIS regime (noting that cloud hosting services may be of particular relevance to data centre operators), it may be necessary to consider these cybersecurity requirements in the UK. There are no current plans to impose direct obligations on data centre operators unlike NIS2 in the EU.
Further, unlike the EU where telecoms security will fall under the scope of the NIS regime, telecoms services in the UK will remain subject to separate telecoms security requirements. The UK has recently implemented a new strengthened telecoms security framework which may be either directly relevant to data centre service operators if they also provide telecoms services or indirectly relevant where managed services are being provided to telecoms providers operating in the UK (i.e these providers may expect their data centre providers to have relevant safeguards, measures, procedures and processes in place as well as seeking to flow down obligations into relevant contracts so as to mitigate security risks as well as require them to complete supplier risk assessments).
KSA - What are the key cybersecurity obligations for data centres in the Kingdom of Saudi Arabia?
While data centre specific regulation was issued by the Communications, Space and Technology Commission (CST) in August 2023, including specific requirements for Data Center Service Providers to address physical security, they made no reference logical security. However, there is a significant weight of existing cybersecurity specific provision in the Kingdom.
In June 2020, the Communications & Information Technology Commission (CITC) issued the Cybersecurity Regulatory Framework for Service Providers in the Information and Communication Technology Sector (the “CRF”). The CRF provides a comprehensive set of cybersecurity requirements to be implemented by Service Providers in the ICT sector. The CRF distinguishes between Service Providers who are classified as Critical National Infrastructure (CNI) who must comply with the Essential Cybersecurity Controls (EEC) issued by the National Cybersecurity Authority (NCA) and those Service Providers who are not so classified who must comply with the CRF.
The CRF set out very detailed controls and requirements touching on Governance, Asset Management, Cybersecurity Risk Management, Logical Security, Physical Security and Third Party Security.
The EEC sets minimum cybersecurity requirements with the presentation of 114 cybersecurity controls for national organisations that are within the EEC scope – government organisations and their companies and private sector organisations owning, operating or hosting Critical National Infrastructures. Critical national infrastructure is defined as “infrastructure whose loss or susceptibility to security violations may result in significant negative impact on the availability, integration or delivery of basic services or may have a significant impact on national security, national defence, the KSA economy or KSA national capabilities”.
The EEC are supported by the Critical Systems Cybersecurity Controls (CSCC) which focus on network segmentation, intrusion detection and the monitoring of critical systems. The CSCC applies to organisations operating critical systems and focuses on systems or networks whose failure, unauthorised change to their operation, unauthorised access to them, or to the data stored or processed by them may result in negative impact on the organisation’s businesses and services availability, or cause negative economic, financial, security or social impacts on the national level. The criteria identified in the CSCC for identifying critical systems are when a failure of that system has a negative impact on national security; a negative impact on the Kingdom’s reputation and public image; a significant financial losses (more than 0.01% of GDP); a negative impact on the services provided to a large number of users (i.e., more than 5% of the population); a loss of lives; an unauthorised disclosure of data that is classified as Top Secret or Secret; or a negative impact on the operations of one or more vital sector.
The Cloud Cybersecurity Controls (CCC) were implemented to secure cloud-based data and applications and are a set of controls addressing data encryption, identity and access management and compliance monitoring.
The Data Cybersecurity Controls include the encryption of sensitive data, access controls, data retention and the requirement for data audits.
Also of significant relevance is the Kingdom’s Personal Data Protection Law (PDPL), which came into force on 14 September 2023 to regulate the use of personal data in KSA giving a year within which to achieve compliance. Accordingly, note in particular that full enforceability begins on 14 September 2024.
While this paper is not the place for a detailed explanation of the PDPL, is it worth identifying that it includes the requirement of the adoption of security measures, including the regular assessment of security controls; identifying and addressing vulnerabilities; assessing system security through penetration testing; continuous security monitoring; and third party risk management.
For more information, please contact Anthony Rosen, Simon Shooter, Dr. Natallia Karniyevich and Hayley Blyth.






