ENISA Implementing Guidance on NIS2 security measures - draft for consultation
On 18 October 2024, the European Commission published the Implementing Regulation laying down rules for the application of the NIS2 Directive as regards technical and methodological requirements of cybersecurity risk-management measures and further specification of the cases in which an incident is considered to be significant with regard to certain types of entities, including cloud computing service providers, data centre service providers, managed (security) service providers, providers of online market places, of online search engines and of social networking services platforms (so-called ‘relevant entities’).
On 7 November 2024, the day when the Implementing Regulation came into force, ENISA published the consultation draft of a 155-pages-long Implementing Guidance, offering non-binding guidance to support relevant entities with implementing these technical and methodological requirements. This in line with the Recital 7 of the NIS2 Directive according to which ENISA can support relevant entities with guidance on the implementation of the technical and methodological requirements referred to in the Implementing Regulation’s Annex.
Importantly, according to the draft Implementing Guidance, beyond the relevant entities to the Regulation, this guidance may provide indications on the technical and the methodological requirements of the cybersecurity risk-management measures of NIS2 Directive, which may be considered useful by other public or private actors in improving their cybersecurity.
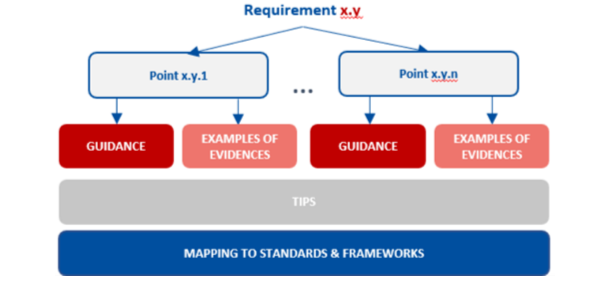
For the technical and methodological requirements, the draft Implementing Guidance contains:
- guidance, i.e., indicative and actionable advice on parameters to consider when implementing a requirement or further explanation to concepts found in the legal text;
- examples of evidence, i.e. the types of evidence that a requirement is in place;
- extra general tips for additional consideration by the entity, where available; and
- mapping correlating each requirement to European and international standards and national frameworks.
The mapping should not be interpreted as a measure of equivalence among different standards or frameworks. It refers to relevant requirements in these standards or frameworks without assessing whether these fully cover the requirements of the regulation. Cybersecurity standards or frameworks often address the same cybersecurity concerns but use different language, structures, or levels of specificity or detail. Understanding these relationships may help relevant entities use and integrate multiple standards or frameworks to maintain compliance, reduce duplication, and streamline audits.
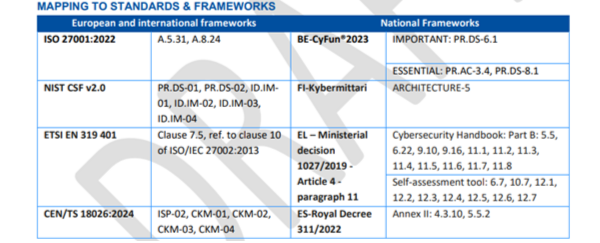
(ENISA draft Implementing Guidance - Mapping table, page 107).
In more detail regarding some of the content of the draft Implementing Guidance:
According to the draft Implementing Guidance, risk assessment results and residual risks shall be accepted by management bodies or, where applicable, by persons who are accountable and have the authority to manage risks, provided that the relevant entities ensure adequate reporting to the management bodies.
The document also details that relevant entities shall establish and implement an incident handling policy, laying down the roles, responsibilities, and procedures for detecting, analysing, containing or responding to, recovering from, documenting, and reporting incidents promptly. The relevant entities shall lay down procedures and use tools to monitor and log activities on their network and information systems to detect events that could be considered incidents and respond accordingly to mitigate the impact; and put in place a simple mechanism allowing their employees, suppliers, and customers to report suspicious events.
According to the draft Implementing Guidance, relevant entities shall lay down and maintain a business continuity and disaster recovery plan to apply in the case of incidents; maintain backup copies of data and provide sufficient available resources, including facilities, network and information systems and staff, to ensure an appropriate level of redundancy, and put in place a process for crisis management.
Addressing supply chain security, the ENISA document identified that relevant entities shall establish, implement, and apply a supply chain security policy that governs the relations with their direct suppliers and service providers to mitigate the identified risks to the security of network and information systems. In the supply chain security policy, the relevant entities shall identify their role in the supply chain and communicate it to their direct suppliers and service providers.
Covering human resources security, the ENISA technical guidance establishes that relevant entities shall ensure that their employees and direct suppliers and service providers, wherever applicable, understand, demonstrate and commit to their security responsibilities, as appropriate for the offered services and the job and in line with the relevant entities’ policy on the security of network and information systems.
On access control, ENISA called upon relevant entities to establish, document, and implement logical and physical access control policies for the access to their network and information systems, based on business requirements as well as network and information system security requirements. The relevant entities shall review and, where appropriate, update the policies at planned intervals and when significant incidents or significant changes to operations or risks occur. Furthermore, the relevant entities shall implement secure authentication procedures and technologies based on access restrictions and the policy on access control.
Next steps: The ENISA draft Implementation Guidance is now available for industry consultation through the following link. The feedback can be provided latest on 9 December 2024, 18.00 CET. Further instructions on how to provide feedback can be found here.
Do you have questions about the Implementing Regulation or the draft Implementing Guidance as well as the impact on your business and the local implementation? Bird & Bird is ready to help you to carry out an assessment of the impact of the cybersecurity legislation on your business and assist in preparing your compliance plan.
For more information, please contact Dr. Natallia Karniyevich.
This article was published in our monthly Connected newsletter, to sign-up to receive future newsletters for the latest Regulatory & Public Affairs news and updates, see below: